Situation Analysis
According to Key Internet Statistics in 2023 (Including Mobile) - BroadbandSearch, there are 5.25 billion+ people on the internet (and growing) who are increasingly challenged by control over their identity – due to the fact that identity authenticity still challenges both the Internet and Web.
Transport Layer Security (TLS) is a globally supported protocol, deployed across every modern computing device, that adds identity authenticity and/or privacy to communications between parties. For instance, it is the crucial component that enables e-commerce.
Communications between the browser used by a shopper and the e-commerce services provided by Amazon.com (and others) is only possible using the server authentication aspect of this protocol.
Unbeknownst to most, the TLS protocol also has a client authentication aspect commonly known as the Client Certificate Authentication (TLS CCA) protocol which enables a server verify credentials presented by a browser on behalf of its user; this aspect of said protocol is crucial to addressing identity authenticity challenges that have afflicted both the Internet and Web since their respective inceptions.
In this post, I use CHAT-GPT to generate a Mermaid Sequence Diagram that illustrates the following:
- Conventional TLS CCA protocol flow
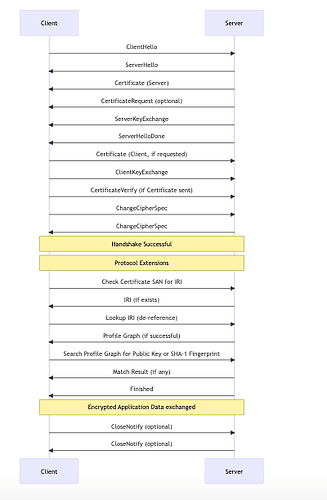
- Extended TLS CCA protocol flow – used by NetIDTLS (for any resolvable identifier) and WebID-TLS (for HTTP-based removable identifiers)
Note:
For maximum impact, especially in regards to generated Tables and Knowledge Graphs, you are encouraged to read this post using a browser that includes the OpenLink Structured Data Sniffer (OSDS) extension (available for Chrome, Edge, Firefox, Safari and others) – thereby enabling you lift the data and information generated into a live Semantic Web that can be saved to any DBMS that supports the SPARQL Query Language & Protocol.
CHAT-GPT Transcript
Q: Describe the TLS-handshake algorithm for Client Certificate Authentication using Mermaid Sequence Notation
A:
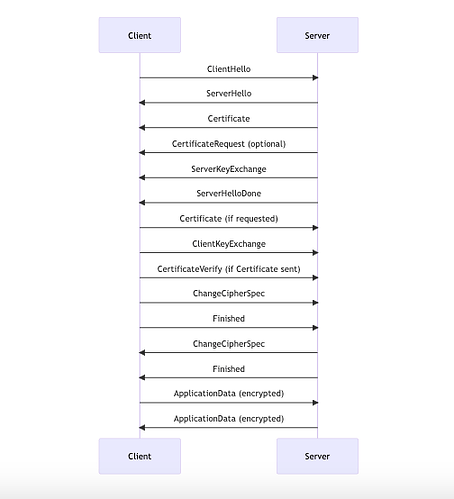
In this Mermaid sequence diagram, we describe the TLS handshake algorithm for Client Certificate Authentication. The main actors are the Client and the Server. The process includes the exchange of messages for establishing a secure connection, including the optional Client Certificate Authentication step.
sequenceDiagram
participant Client
participant Server
Client->>Server: ClientHello
Server->>Client: ServerHello
Server->>Client: Certificate
Server->>Client: CertificateRequest (optional)
Server->>Client: ServerKeyExchange
Server->>Client: ServerHelloDone
Client->>Server: Certificate (if requested)
Client->>Server: ClientKeyExchange
Client->>Server: CertificateVerify (if Certificate sent)
Client->>Server: ChangeCipherSpec
Client->>Server: Finished
Server->>Client: ChangeCipherSpec
Server->>Client: Finished
Client->>Server: ApplicationData (encrypted)
Server->>Client: ApplicationData (encrypted)
Mermaid Sequence Diagram Visualization
Here’s the Live Diagram.
Explanation
Q: Present the following text in a code-block using a Table expressed in Markdown
ClientHello: The client initiates the handshake by sending a message containing the supported TLS version, a random value, and a list of supported cipher suites.
ServerHello: The server responds with its chosen TLS version, a random value, and the chosen cipher suite.
Certificate: The server sends its certificate, which contains the public key.
CertificateRequest (optional): The server requests the client’s certificate if it requires client authentication.
ServerKeyExchange: The server sends a key exchange message containing the necessary parameters for the client to generate the pre-master secret.
ServerHelloDone: The server indicates that it has completed the initial handshake messages.
Certificate (if requested): The client sends its certificate if the server has requested it.
ClientKeyExchange: The client sends the key exchange message containing the encrypted pre-master secret.
CertificateVerify (if Certificate sent): The client sends a digitally signed hash of all the handshake messages exchanged so far, using the private key associated with the provided client certificate.
ChangeCipherSpec: The client signals that all subsequent messages will be encrypted with the negotiated cipher suite and keys.
Finished: The client sends a message containing a hash of all the handshake messages exchanged so far, encrypted with the negotiated keys.
ChangeCipherSpec: The server signals that all subsequent messages will be encrypted with the negotiated cipher suite and keys.
Finished: The server sends a message containing a hash of all the handshake messages exchanged so far, encrypted with the negotiated keys.
ApplicationData (encrypted): The client and server can now exchange encrypted application data using the established secure connection.
Please note that this Mermaid sequence diagram is a high-level overview of the TLS handshake algorithm for Client Certificate Authentication. There are more detailed aspects and variations to the process that are not depicted here.
A:
| Step # | Message/Action | Description |
|---|---|---|
| 1 | ClientHello | Client initiates handshake with supported TLS version, random value, and list of supported cipher suites. |
| 2 | ServerHello | Server responds with chosen TLS version, random value, and chosen cipher suite. |
| 3 | Certificate | Server sends its certificate, which contains the public key. |
| 4 | CertificateRequest (optional) | Server requests the client’s certificate if it requires client authentication. |
| 5 | ServerKeyExchange | Server sends a key exchange message with necessary parameters for client to generate pre-master secret. |
| 6 | ServerHelloDone | Server indicates completion of initial handshake messages. |
| 7 | Certificate (if requested) | Client sends its certificate if the server has requested it. |
| 8 | ClientKeyExchange | Client sends key exchange message with encrypted pre-master secret. |
| 9 | CertificateVerify (if sent) | Client sends digitally signed hash of all handshake messages exchanged so far, using its private key. |
| 10 | ChangeCipherSpec | Client signals that subsequent messages will be encrypted with the negotiated cipher suite and keys. |
| 11 | Finished | Client sends a message with a hash of all handshake messages exchanged so far, encrypted with negotiated keys. |
| 12 | ChangeCipherSpec | Server signals that subsequent messages will be encrypted with the negotiated cipher suite and keys. |
| 13 | Finished | Server sends a message with a hash of all handshake messages exchanged so far, encrypted with negotiated keys. |
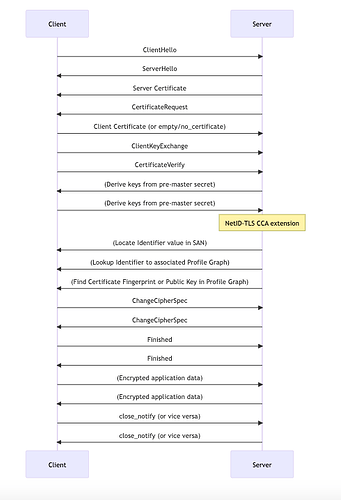
Q: Redo, but extend the algorithm concluding the handshake after the following:
Lookup of Subject Alternative Name value if it is an IRI
A:
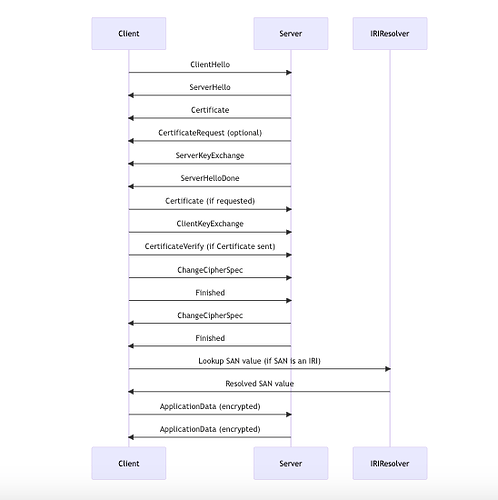
In this Mermaid sequence diagram, we extend the TLS handshake algorithm for Client Certificate Authentication by adding a lookup for the Subject Alternative Name (SAN) value if it’s an Internationalized Resource Identifier (IRI). The main actors are the Client, the Server, and a third participant - the IRI Resolver.
sequenceDiagram
participant Client
participant Server
participant IRIResolver
Client->>Server: ClientHello
Server->>Client: ServerHello
Server->>Client: Certificate
Server->>Client: CertificateRequest (optional)
Server->>Client: ServerKeyExchange
Server->>Client: ServerHelloDone
Client->>Server: Certificate (if requested)
Client->>Server: ClientKeyExchange
Client->>Server: CertificateVerify (if Certificate sent)
Client->>Server: ChangeCipherSpec
Client->>Server: Finished
Server->>Client: ChangeCipherSpec
Server->>Client: Finished
Client->>IRIResolver: Lookup SAN value (if SAN is an IRI)
IRIResolver->>Client: Resolved SAN value
Client->>Server: ApplicationData (encrypted)
Server->>Client: ApplicationData (encrypted)
Mermaid Sequence Diagram Visualization
Here’s the Live Diagram.
Explanation
Q: Create a rendition of the following, using a Table expressed in Markdown, that’s output to a code-block.
In this extended TLS handshake algorithm, the client looks up the SAN value if it’s an IRI after the handshake is completed. The IRI Resolver is a third participant that helps resolve the SAN value if needed.
1-12: Follow the same steps as in the original TLS handshake algorithm with Client Certificate Authentication.
Lookup SAN value (if SAN is an IRI): If the SAN value in the server certificate is an IRI, the client performs a lookup to resolve the IRI using the IRI Resolver.
Resolved SAN value: The IRI Resolver returns the resolved SAN value to the client.
15-16: The client and server continue exchanging encrypted application data using the established secure connection.
Please note that this Mermaid sequence diagram is a high-level overview of the extended TLS handshake algorithm for Client Certificate Authentication with SAN IRI lookup. There are more detailed aspects and variations to the process that are not depicted here.
A:
| Step # | Message/Action | Description |
|---|---|---|
| 1 | ClientHello | Client initiates handshake with supported TLS version, random value, and list of supported cipher suites. |
| 2 | ServerHello | Server responds with chosen TLS version, random value, and chosen cipher suite. |
| 3 | Certificate | Server sends its certificate, which contains the public key. |
| 4 | CertificateRequest (optional) | Server requests the client’s certificate if it requires client authentication. |
| 5 | ServerKeyExchange | Server sends a key exchange message with necessary parameters for client to generate pre-master secret. |
| 6 | ServerHelloDone | Server indicates completion of initial handshake messages. |
| 7 | Certificate (if requested) | Client sends its certificate if the server has requested it. |
| 8 | ClientKeyExchange | Client sends key exchange message with encrypted pre-master secret. |
| 9 | CertificateVerify (if sent) | Client sends digitally signed hash of all handshake messages exchanged so far, using its private key. |
| 10 | ChangeCipherSpec | Client signals that subsequent messages will be encrypted with the negotiated cipher suite and keys. |
| 11 | Finished | Client sends a message with a hash of all handshake messages exchanged so far, encrypted with negotiated keys. |
| 12 | ChangeCipherSpec | Server signals that subsequent messages will be encrypted with the negotiated cipher suite and keys. |
| 13 | Finished | Server sends a message with a hash of all handshake messages exchanged so far, encrypted with negotiated keys. |
| 14 | Lookup SAN (if SAN is an IRI) | Client performs a lookup for the SAN value in the server certificate if it’s an IRI. |
| 15 | ApplicationData (encrypted) | Client and server can now exchange encrypted application data using the established secure connection. |
Q:
Generate an RDF-Turtle rendition, in HowTo and Step-By Guide form, using the following guidelines:
- Place code within
## Turtle Start ##and## Turtle End ##block - Use terms from Schema.org
- Ensure each step is named via a schema:name attribute
- Use schema:position and schema:nextItem for enhanced indexing and flow
- Use hash-based IRIs ( with @base set to <> ) for subject and object denotation
- Include DBpedia cross-references where such exist, confined to the schema:HowTo instance description, bearing in mind this is about PKI, Cryptography, Privacy, TLS, HTTPS, Digital Identity, Privacy, and Data Security
A:
## Turtle Start ##
@prefix schema: <http://schema.org/> .
@prefix dbo: <http://dbpedia.org/ontology/> .
@prefix dbr: <http://dbpedia.org/resource/> .
<#HowTo>
a schema:HowTo ;
schema:name "TLS Handshake and Secure Communication Process" ;
schema:step <#Step1> ;
dbo:subject dbr:Transport_Layer_Security, dbr:HTTPS, dbr:Public_key_infrastructure, dbr:Privacy, dbr:Data_security .
<#Step1>
a schema:HowToStep ;
schema:name "Client sends ClientHello message to the server" ;
schema:position 1 ;
schema:nextItem <#Step2> .
<#Step2>
a schema:HowToStep ;
schema:name "Server responds with ServerHello message and Certificate" ;
schema:position 2 ;
schema:nextItem <#Step3> .
<#Step3>
a schema:HowToStep ;
schema:name "Server optionally requests Certificate and sends ServerKeyExchange" ;
schema:position 3 ;
schema:nextItem <#Step4> .
<#Step4>
a schema:HowToStep ;
schema:name "Server sends ServerHelloDone message" ;
schema:position 4 ;
schema:nextItem <#Step5> .
<#Step5>
a schema:HowToStep ;
schema:name "Client responds with Certificate (if requested), ClientKeyExchange, CertificateVerify (if Certificate sent), ChangeCipherSpec, and Finished messages" ;
schema:position 5 ;
schema:nextItem <#Step6> .
<#Step6>
a schema:HowToStep ;
schema:name "Server responds with ChangeCipherSpec and Finished messages" ;
schema:position 6 ;
schema:nextItem <#Step7> .
<#Step7>
a schema:HowToStep ;
schema:name "Client looks up SAN value (if SAN is an IRI)" ;
schema:position 7 ;
schema:nextItem <#Step8> .
<#Step8>
a schema:HowToStep ;
schema:name "IRIResolver returns the resolved SAN value" ;
schema:position 8 ;
schema:nextItem <#Step9> .
<#Step9>
a schema:HowToStep ;
schema:name "Client and Server exchange ApplicationData (encrypted)" ;
schema:position 9 .
## Turtle End ##
OpenLink Structured Data Sniffer Options
- Google Chrome Store for Chromium-based Browsers
- Mozilla Store for Firefox
- Mac App Store for Safari
- Github Open Source Repository
Related
- Web, Logic, Sentences, and the Magic of Being You! | OpenLink Virtuoso Weblog | Medium
- How-To Guide— Self-Sovereign Identity using NetID-TLS via a YouID-Generated Profile Document
- HowTo – Using CHAT-GPT to generate a Mermaid Sequence Diagram about Digitally Signed Email using the S/MIME via Apple Mail
- HowTo — Using CHAT-GPT to generate a Knowledge Graph from a Mermaid Entity Relationship Model Diagram
- ChatGPT Nanotations Collections – these docs combine prompts and the structured data generated by answers that double as LOD Cloud Knowledge Graph and Semantic Web entry points
- ChatGPT Prompt Collection
- ChatGPT Prompt Collection RSS Feed
- ChatGPT Prompt Collection Atom Feed