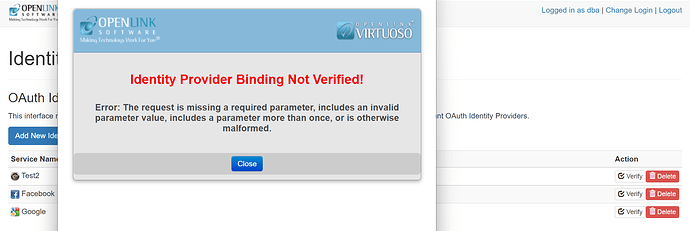
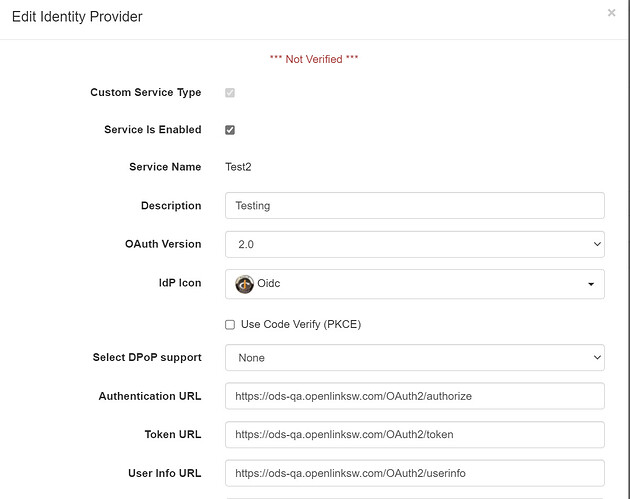
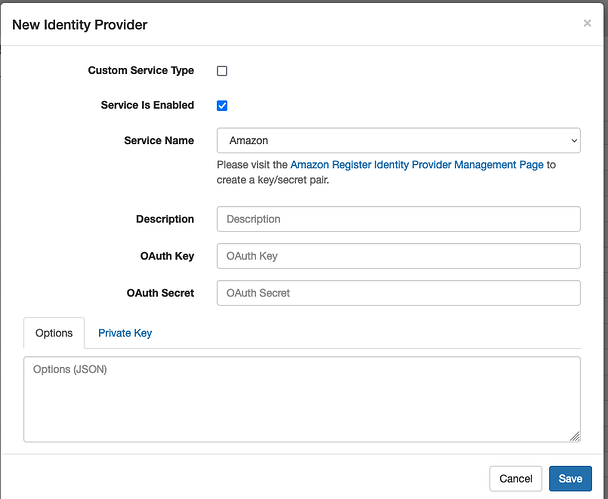
I have an application that needs to use OIDC on the Virtuoso platform. I have been using the referenced article OpenID Connect (OIDC) and OAuth Protocol Virtualization, using Virtuoso | by Kingsley Uyi Idehen | OpenLink Virtuoso Weblog | Medium as a guide. At the point where I have to ‘Add OAuth Client API Key’, I get the following error message:
What is the OIDC service you are seeking to ‘Add OAuth Client API Key’ for and what are the other parameters being passed in the New Identity Provider dialog , as one of them seem to be invalid/incorrect ?
Where did you generate the OAuth key & secret from ?
From Google developer portal
Are you then seeking to use Google as the IdP ? In which case we have a build in service for configuration against Google as detailed at How To: Add Google Sign In (Identity Provider) Services to Virtuoso's Authentication Layer (VAL)
Fundamentally, what are you trying to achieve?
For instance, are you trying to protect a specific service whereby identity principals (users) are authenticated using OpenID Connect as a bridge to a variety of Identity Authentication Service Providers?
For instance, what you see at Protected SPARQL Query Service, when you click on the “login” link?
Related
Yes @kidehen this is what I am trying to achieve and have been using this same link you shared as a guide, but I think I am doing something wrong at the point where I need to add OAuth client and API key
If so, what’s failing?
Is it the verification stage following registration of a 3rd Part Identity Provider (Idp)? Note, each of the buttons in the Virtuoso Authentication Layer dialog map to a 3rd party Authentication Services Provider.
For instance, is Google the IdP you are trying to setup here?
Are you trying to setup Google as your IdP, for instance? I can see from the dialog that your binding is problematic, hence the error.
Yes is the verification page that is failing
Yes I am trying to set up Google as the idp and can not figure what I am doing wrong at the moment from the binding
Again, like you said earlier on, what I am trying to achieve is to write a client-side script as a demo for now that will interface with Virtuoso over HTTPS and access relevant IAM services of the OIDC and OAuth2 protocols, perform an identity enrollment and verification, request an authentication, and get an authorization token. I need to understand this implementation with this demo I am creating before implementing it with the main service
Okay, so you are trying to register Google as an Identity Authentication Services provider (IdP) for your Virtuoso instance. If so, I assume you took the following route:
-
http://{your-instance-cname}/oauth/admin.vsp or the Web Services | Authentication Services Binding menu path using the HTML-based the Virtuoso Admin Interface (a/k/a “The Conductor”)
-
Attempted to configure your Google IdP using the Client ID and Shared Secret obtained from Google
If that’s all correct, then you would be entering those credentials using either admin interface, as per the screenshots that follow.
The Reactive Admin Interface at http://{your-instance-cname}/oauth/admin.vsp
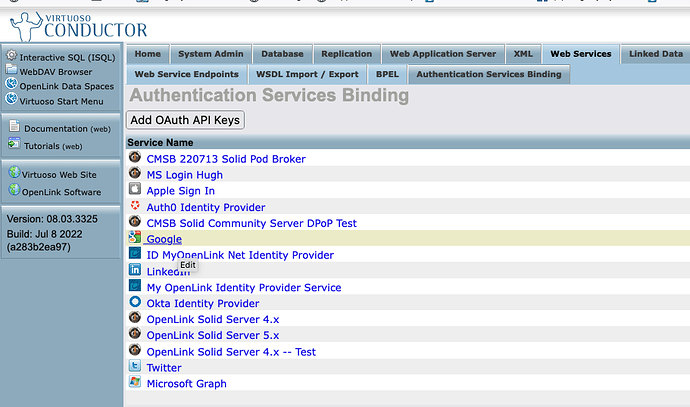
First page in sequence, where you click on the “Add New Identity Provider” button.
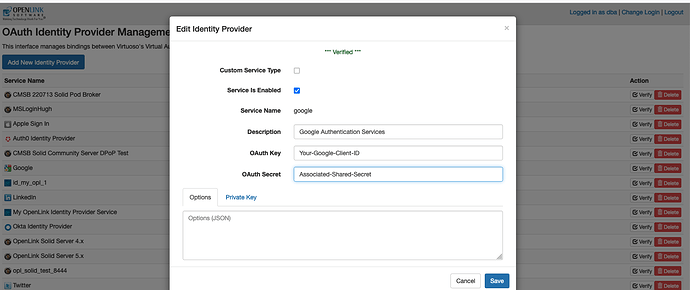
In the next page presented, select Google from the drop-down.
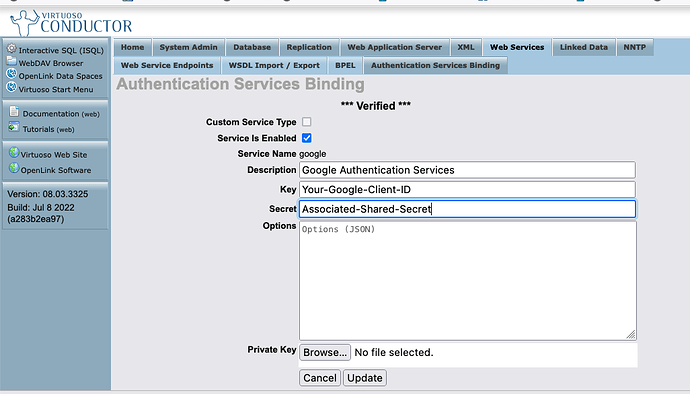
Following selection of Google, enter credentials for your instance (i.e., the Google Client)
Once the input fields are completed, save and retest.
The HTML-based Conductor Interface
Initial page.
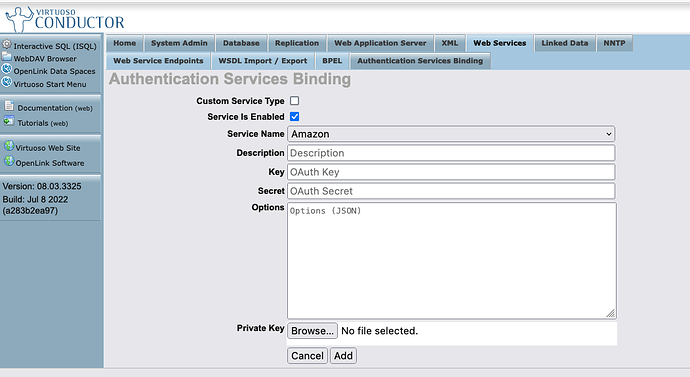
Click on Add OAuth API Keys button, and then select Google from the drop-down.
Following selection of Google, enter credentials for your instance (i.e., the Google Client)
Once the input fields are completed, save and retest.
Related
Thanks @kidehen for this detailed explanation, it is now working fine as expected
How do I write a VSP script and use it to access this service?
Before jumping into writing a VSP, can you confirm that you are now successfully authenticating against your SPARQL endpoint using Google as the Identity Authentication Services Provider?
Also, are you building a VSP-based application or developing using .NET Frameworks? I ask because OpenID Connect is a protocol for matching Relying Parties (Apps) to Identity Authentication Service Providers i.e., you have Dynamic and Manual bindings available via your chosen development environment.
SeeAlso
Yes I can successfully authenticate against my SPARQL endpoint using Google as the Identity Authentication Services Provider, and I am using .NET Core Framework for the application I am building.
So your next step isn’t about a VSP that authenticates using OpenID Connect + OAuth, but a .NET Core Framework interaction with your Virtuoso instance that entails:
- Registering you App with the Virtuoso Instance as a Relying Party for Identity Authentication Services (i.e., as a client)
- Testing authentication from your .NET app against your Virtuoso instance.
See:
Your Virtuoso Instance is just another Identity Authentication Services Provider like Google, Facebook etc., in that example.
Okay, thanks @kidehen for the clarity, so how do I go about registering my App with the Virtuoso instance I have, is the same way I added new identity provider to my SPARQL endpoint or is a different process.