Here are the steps for integrating Keycloak’s Identity Provider Services into VAL i.e., Keycloak’s OpenID Connect Compliant Identity Provider (IdP) functionality as one of the IdP options exposed via VAL.
Conceptually, the process is as follows:
- Register your VAL-enabled Virtuoso instance as an Application (the Relying Party) with Keycloak’s Identity Provider Services
- Add Keycloak’s Identity Provider to the the collection of IdPs registered with your VAL-enabled Virtuoso instance .
Application (Relying Party) Registration Related Steps
- Register an Application with Keycloak (you must have a Keycloak user account)
- Register your Application which includes Naming and setting up a Callback/Redirect URL (
https://{cname}/val/api/thirdparty_callback)
- Generate a Client Shared Secret (Private Key) for your App
At this juncture you have an Application Client ID and its associated Shared Secret in place for authentication against Keycloak user accounts.
VAL Setup Steps
This is achieved via the Conductor or OAuth IdP Admin UI (https:/{your-instance-cname}/oauth/admin.vsp).
- Goto the VAL Admin page
https://{cname}/oauth/admin.vsp
-
Click on the
Add New Identity Providerbutton -
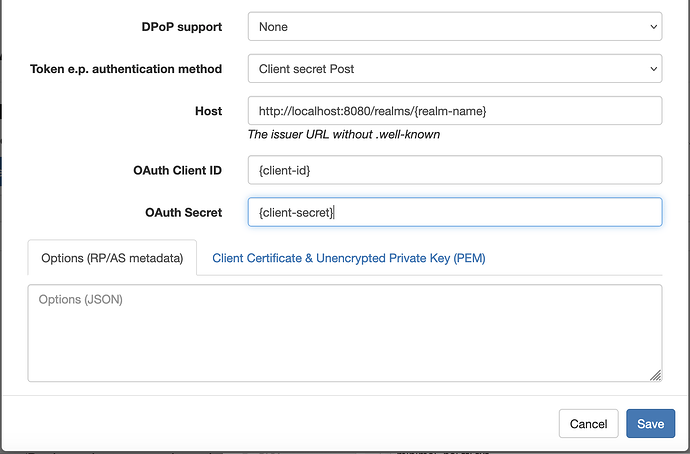
Fill in the
Service Name, Keycloak issuerHostname iehttp://{CNAME}/realms/{realm}, ApplicationOAuth Client ID,OAuth SecretandSavethe settings.
- Click the
Verifybutton to verify the binding to the created Keyclock IdP service.
- Test VAL authentication via the SPARQL endpoint or other services that use VAL for authentication by selecting the now available Keycloak IdP
OIDCicon in the VAL Login Dialog, for authentication with the Keycloak user account associated with theclient id & secretof the IdP service added.