Okay, so you are trying to register Google as an Identity Authentication Services provider (IdP) for your Virtuoso instance. If so, I assume you took the following route:
-
http://{your-instance-cname}/oauth/admin.vsp or the Web Services | Authentication Services Binding menu path using the HTML-based the Virtuoso Admin Interface (a/k/a “The Conductor”)
-
Attempted to configure your Google IdP using the Client ID and Shared Secret obtained from Google
If that’s all correct, then you would be entering those credentials using either admin interface, as per the screenshots that follow.
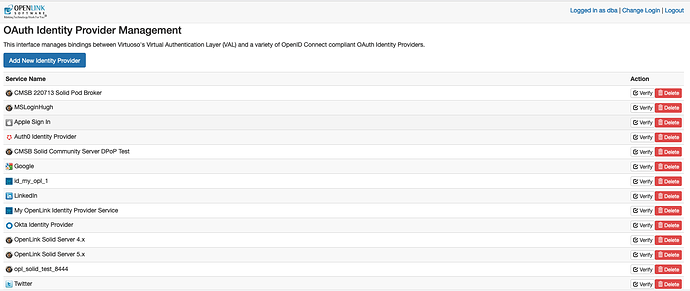
The Reactive Admin Interface at http://{your-instance-cname}/oauth/admin.vsp
First page in sequence, where you click on the “Add New Identity Provider” button.
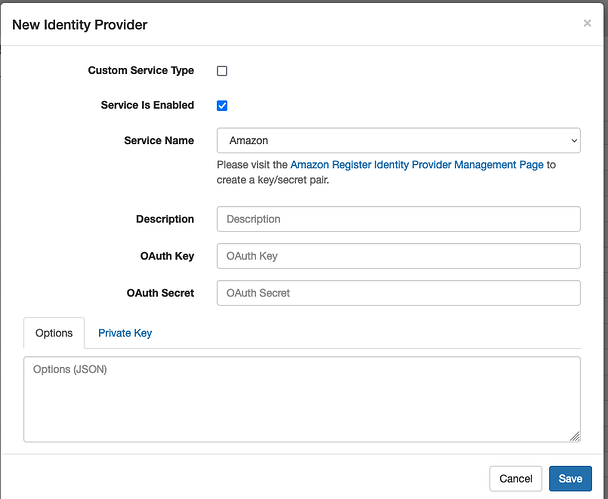
In the next page presented, select Google from the drop-down.
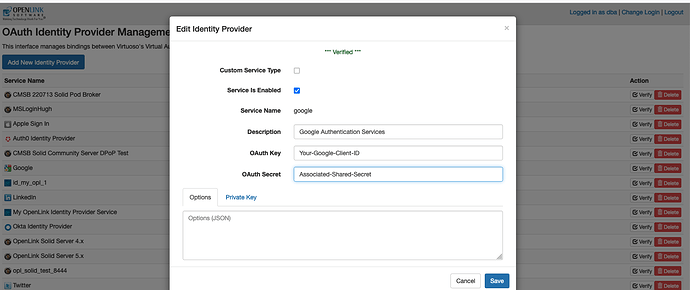
Following selection of Google, enter credentials for your instance (i.e., the Google Client)
Once the input fields are completed, save and retest.
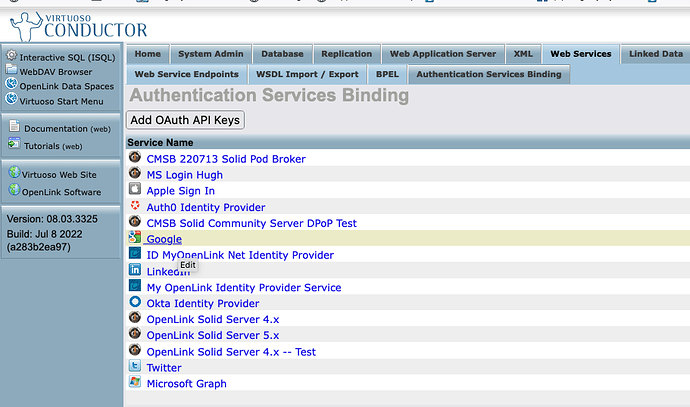
The HTML-based Conductor Interface
Initial page.
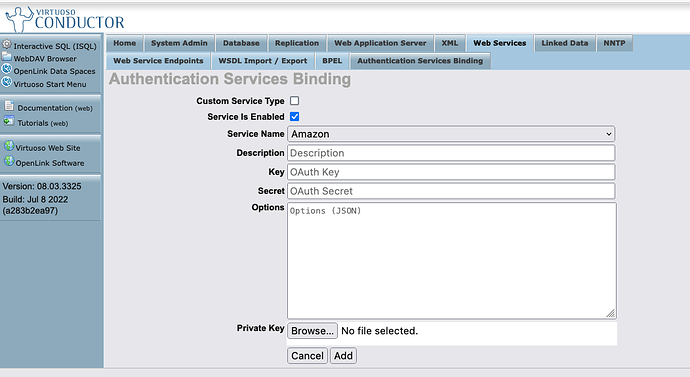
Click on Add OAuth API Keys button, and then select Google from the drop-down.
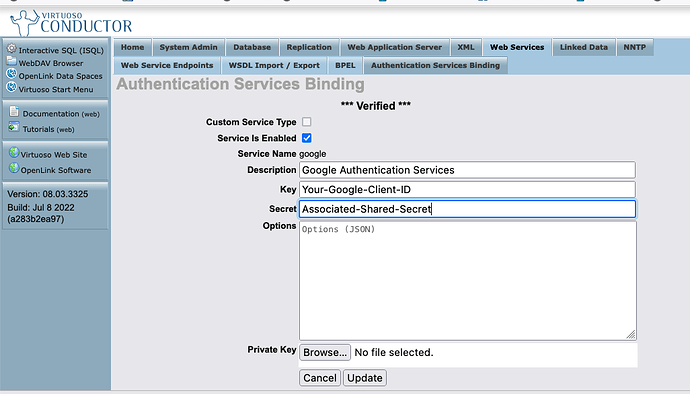
Following selection of Google, enter credentials for your instance (i.e., the Google Client)
Once the input fields are completed, save and retest.