Hi,
the Oauth is working properly with a localhost CURL but not with the HOST CURL
**Error was: 11:46:00 Failed HTTP listen at HOST:443 code (-6). **
Ex:
curl -I https://localhost/oauth/index.vsp -k -v
- Trying ::1…
- TCP_NODELAY set
- connect to ::1 port 443 failed: Connection refused
- Trying 127.0.0.1…
- TCP_NODELAY set
- Connected to localhost (127.0.0.1) port 443 (#0)
- ALPN, offering h2
- ALPN, offering http/1.1
- successfully set certificate verify locations:
- CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none - TLSv1.3 (OUT), TLS handshake, Client hello (1):
- TLSv1.3 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (IN), TLS handshake, Certificate (11):
- TLSv1.2 (IN), TLS handshake, Server key exchange (12):
- TLSv1.2 (IN), TLS handshake, Request CERT (13):
- TLSv1.2 (IN), TLS handshake, Server finished (14):
- TLSv1.2 (OUT), TLS handshake, Certificate (11):
- TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
- TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
- TLSv1.2 (OUT), TLS handshake, Finished (20):
- TLSv1.2 (IN), TLS handshake, Finished (20):
- SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384
- ALPN, server did not agree to a protocol
- Server certificate:
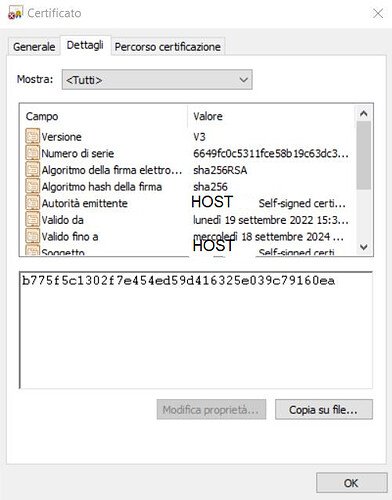
- subject: C=XX; ST=XXXX; O=XXXX; OU=XXXX; CN=localhost; emailAddress=xxx@xxxx.xx
- start date: Sep 16 07:41:07 2022 GMT
- expire date: Sep 16 07:41:07 2023 GMT
- issuer: C=IT; ST=XXX; OXXX; OU=XXXX; CN=XX; emailAddress=xxx@xxxx.xx
- SSL certificate verify result: unable to get local issuer certificate (20), continuing anyway.
HEAD /oauth/index.vsp HTTP/1.1
HEAD /oauth/index.vsp HTTP/1.1
Host: localhost
User-Agent: curl/7.61.1
Accept: /
- TLSv1.2 (IN), TLS handshake, Hello request (0):
- TLSv1.2 (OUT), TLS handshake, Client hello (1):
- TLSv1.2 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (IN), TLS handshake, Certificate (11):
- TLSv1.2 (IN), TLS handshake, Server key exchange (12):
- TLSv1.2 (IN), TLS handshake, Request CERT (13):
- TLSv1.2 (IN), TLS handshake, Server finished (14):
- TLSv1.2 (OUT), TLS handshake, Certificate (11):
- TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
- TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
- TLSv1.2 (OUT), TLS handshake, Finished (20):
- TLSv1.2 (IN), TLS handshake, Finished (20):
< HTTP/1.1 200 OK
HTTP/1.1 200 OK
But:
curl -I https://HOST/oauth/index.vsp -k -v
- Trying HOST…
- TCP_NODELAY set
- Connected to HOST (HOST) port 443 (#0)
- ALPN, offering h2
- ALPN, offering http/1.1
- successfully set certificate verify locations:
- CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none - TLSv1.3 (OUT), TLS handshake, Client hello (1):
- TLSv1.3 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (IN), TLS handshake, Certificate (11):
- TLSv1.2 (IN), TLS handshake, Server key exchange (12):
- TLSv1.2 (IN), TLS handshake, Request CERT (13):
- TLSv1.2 (IN), TLS handshake, Server finished (14):
- TLSv1.2 (OUT), TLS handshake, Certificate (11):
- TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
- TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
- TLSv1.2 (OUT), TLS handshake, Finished (20):
- TLSv1.2 (IN), TLS handshake, Finished (20):
- SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384
- ALPN, server did not agree to a protocol
- Server certificate:
- subject: C=XX; ST=XXXX; O=XXXX; OU=XXXX; CN=localhost; emailAddress=xxx@xxxx.xx
- start date: Sep 16 07:41:07 2022 GMT
- expire date: Sep 16 07:41:07 2023 GMT
- issuer: C=IT; ST=XXX; OXXX; OU=XXXX; CN=XX; emailAddress=xxx@xxxx.xx
- SSL certificate verify result: unable to get local issuer certificate (20), continuing anyway.
HEAD /oauth/index.vsp HTTP/1.1
Host: HOST
User-Agent: curl/7.61.1
Accept: /
< HTTP/1.1 403 Forbidden
HTTP/1.1 403 Forbidden
What is the reason ?