In OAuth admin, we need key and secret for the identity providers.
We also need to provide public URLs in the process of registering our application with these identity providers. However, our public IP is not working with the SSL setup.
The SSL setup works only with localhost at the moment.
Can it be made to work with our public IP or should we point our public IP to a domain / subdomain name before configuring SSL?
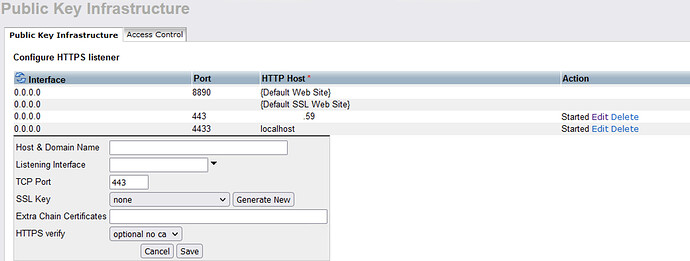
How specifically have you setup the HTTPS Listener, please detail the steps performed ?
Did you not setup the HTTPS listener with a hostname of the public IP address you want it to be accessible on ? As it sounds like the hostname has been set to localhost …
What is the HTTP Host entry of .59 in your screenshot above ? As I would assume that it should be the indicated public IP you want to expose the Virtuoso HTTPS listener on the default 443 port , but .59 is not a valid IP address and should be edited and set to a valid IP address …
You have exposed localhost:4443 for accessing the HTTPS listener on localhost , which I presume is what you say can be successfully accessed ?
I blurred out some part of the complete public IP. Your other presumption is right. Based on what has been done (with the actual public IP) should that be okay for what we want to achieve? Or what more is to be modified or included? Should the localhost be deleted?
You should have said some of the public IP address was blurred out …
Both the *59* and and localhost HTTPS listeners are listed as Started in the screen shot provide and thus if the public IP address is correct setup for remote/public access with your network, then it should be accessible as the localhost listener is.
Thank you.
In order to achieve what we initially started out i.e. registering our application with identity providers, we figured out that using a self signed certificate will not work with a public IP.
I would please like to know if we should proceed with purchasing an SSL certificate from a certificate authority and if yes, what steps are we to take after the purchase?
A valid CA rather than self signed certificate would typically be required use is registering with an official external identity provider that will want to validate authenticity.
Any externally provided certificate can be imported into Virtuoso via the Conductor to the “dba” user account after which it will be accessible within Virtuoso as an internally generated self signed certificate is, as detailed in this CA Keys Import using Conductor document.
Thank you.
I would also please like to know how to setup a domain name on Virtuoso (i.e. connecting the current public IP with a domain name) and how to install the SSL for the domain name.
Not sure what you are asking, the public IP would be associated with a domain name in your DNS server and then a HTTPS listener created in Virtuoso using either the public IP address or domain name, for processing incoming requests to the domain name.
As said in previous post, any externally provided certificate can be imported into Virtuoso via the Conductor to the dba user account after which it will be accessible within Virtuoso as an internally generated self signed certificate is, as detailed in this CA Keys Import using Conductor document.
Good day, I purchased an SSL certificate, and imported it using the steps in the link. However, I cannot access the URL via https even though it works via http.
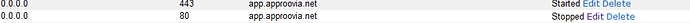
Kindly advise on what next to do.
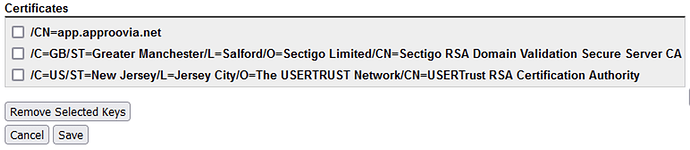
Which of the 3 listed certificates is being used by the app.approovia.net HTTPS listener on port 443, this can be seen if you click on the edit link for the listener ?
Also, what is in the virtuoso.log as it should show on startup if the selected certificate is loaded successfully and when it is stopped and started ie something like:
...
09:42:04 Checkpoint finished, log reused
09:42:06 SSL: Using X509 client CA /C=US/O=DigiCert Inc/CN=DigiCert TLS RSA SHA256 2020 CA1
09:42:06 SSL: Using X509 client CA /C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA
09:42:06 HTTP/WebDAV server online at 8890
09:42:06 HTTPS server online at :443
09:42:06 Server online at 1111 (pid 1722)
09:44:14 HTTPS server offline at :443
09:47:09 HTTPS server online at :443