Good day, I tried to follow the steps from http://docs.openlinksw.com/virtuoso/webserverhttpslistenerset/ and I am not very clear on the Self Signed Certificate aspect. Is it possible for this to be explained?
Another question is: what is meant by Wed ID in this context?
What about the Self Signed Certificate aspects is unclear ?
Virtuoso itself can used a Certificate Authority, for the generation of its own Self Signed Certificates for use in setting up secure HTTPS and SQL SSL access to its services.
A WebID is a way to uniquely identify a person, company, organisation, or other agent using a URI. With Virtuoso WebID Protocol Support detailed in the documentation.
Thanks hwilliams, while trying to follow the steps provided, I randomly get:
License has expired URI = ‘/DAV/VAD/conductor/account_create.vspx’
What to do you think could be the issue and a possible solution?
Do you not have a valid Virtuoso license file in place for installation, which is require for the OpenLink License Manager service to allow continuous connections to the database. As if not then on starting the Virtuoso commercial edition it will use the Built-in Virtuoso Demo License , that runs with the indicated restrictions for about 10mins and the would start giving the license expired message requiring a restart, which sounds like the issue you are hitting. If you check the virtuoso.log file you will probably see the occurrences of the demo license being activated on startup or you have an evaluation license in place that has genuinely expired.
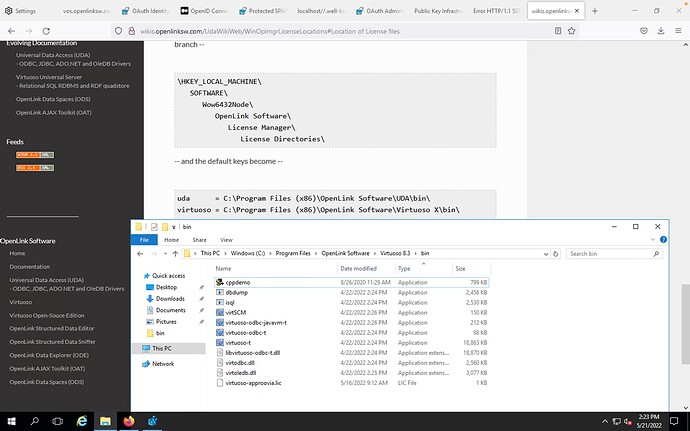
Thank you. We actually have a valid license. Checking all the locations based on your advise shows the following:
Yet the issue still remains. Kindly advise on what to do to resolve this.
In your directory listing the file same is virtuoso-approvia.lic whereas for Virtuoso the license file MUST be called virtuoso.lic, thus you need to rename and restart Virtuoso for it to be picked up …
Setting up HTTPS on the server side requires an X.509 certificate for server identification.
A self-signed certificate is one that isn’t issued by a 3rd party issuer (a/k/a Certificate Authority) – which would be the case if you make use of Virtuoso’s built-in X.509 certificate generation functionality.
The HTTP-based URI placed in the Subject Alternate Name (SAN) slot of an X.509 Certificate. If you are using Virtuoso’s built-in certificate generator, this would take the form of a hyperlink that names a person, organization, of a piece of software.
A WebID is used by the WebID-TLS and NetID-TLS protocols to identity authentication, and it only comes into play if you are setting Virtuoso up to authenticate using the aforementioned protocols.