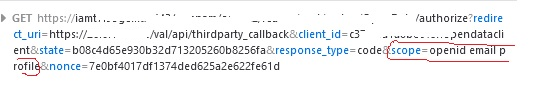
Hi @cblakeley and @hwilliams finally I found the problem, the curl send to IAM gives an error:
C:>curl "https://iam.it:8443/openam/oauth2/realms/root/realms/OpenData/authorize?redirect_uri=https://<ip>/val/api/thirdparty_callback&client_id=xxxxxxx.opendataclient&state=85ee872d7b81b5b5902a2f4926460ecf&response_type=code&scope=openid^%^20email^%^20profile&nonce=c20964d3bf5028ca156c06ef97319505" -H "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7" -H "Accept-Encoding: gzip, deflate, br" -H "Accept-Language: it-IT,it;q=0.9" -H "Connection: keep-alive" -H "Cookie: OAUTH_REQUEST_ATTRIBUTES=eyJzY29wZSI6Im9wZW5pZCBlbWFpbCBwcm9maWxlIiwicmVzcG9uc2VfdHlwZSI6ImNvZGUiLCJyZWRpcmVjdF91cmkiOiJodHRwczovLzI2LjAuMTg5LjE4OC92YWwvYXBpL3RoaXJkcGFydHlfY2FsbGJhY2siLCJzdGF0ZSI6Ijg1ZWU4NzJkN2I4MWI1YjU5MDJhMmY0OTI2NDYwZWNmIiwibm9uY2UiOiJjMjA5NjRkM2JmNTAyOGNhMTU2YzA2ZWY5NzMxOTUwNSIsImNsaWVudF9pZCI6ImMzNzg2ZmExYTBiZWM0OGYub3BlbmRhdGFjbGllbnQifQ==; amlbcookie=01; SIAMTHS=dwX5S3EfsAH9YIxlE2jhpqkD9g8.*AAJTSQACMDIAAlNLABwwRUcxNGJJbWNBSjVQRjA5aXpkSnoyRkNuMDA9AAR0eXBlAANDVFMAAlMxAAIwMQ..*" -H "Referer: https://iamt7.it:8443/openam/XUI/?realm=/OpenData&goto=https://iam.it::8443/openam/oauth2/realms/root/realms/OpenData/authorize?redirect_uri^%^3Dhttps://2<ip>/val/api/thirdparty_callback^%^26client_id^%^3Dc3786fa1a0bec48f.opendataclient^%^26state^%^3D85ee872d7b81b5b5902a2f4926460ecf^%^26response_type^%^3Dcode^%^26scope^%^3Dopenid^%^2520email^%^2520profile^%^26nonce^%^3Dc20964d3bf5028ca156c06ef97319505" -H "Sec-Fetch-Dest: document" -H "Sec-Fetch-Mode: navigate" -H "Sec-Fetch-Site: same-origin" -H "Sec-Fetch-User: ?1" -H "Upgrade-Insecure-Requests: 1" -H "User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36" -H "sec-ch-ua: ""Not_A Brand"";v=""8"", ""Chromium"";v=""120"", ""Google Chrome"";v=""120""" -H "sec-ch-ua-mobile: ?0" -H "sec-ch-ua-platform: ""Windows"""
<!doctype html><html lang="en"><head><title>HTTP Status 400 – Bad Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400 – Bad Request</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> Invalid character found in the request target [/openam/oauth2/realms/root/realms/OpenData/authorize?redirect_uri=https://26.0.189.188/val/api/thirdparty_callback&client_id=c3786fa1a0bec48f.opendataclient&state=85ee872d7b81b5b5902a2f4926460ecf&response_type=code&scope=openid^%^20email^%^20profile&nonce=c20964d3bf5028ca156c06ef97319505]. The valid characters are defined in RFC 7230 and RFC 3986</p><p><b>Description</b> The server cannot or will not process the request due to something that is perceived to be a client error (e.g., malformed request syntax, invalid request message framing, or deceptive request routing).</p><p><b>Exception</b></p><pre>java.lang.IllegalArgumentException: Invalid character found in the request target [/openam/oauth2/realms/root/realms/OpenData/authorize?redirect_uri=https://26.0.189.188/val/api/thirdparty_callback&client_id=c3786fa1a0bec48f.opendataclient&state=85ee872d7b81b5b5902a2f4926460ecf&response_type=code&scope=openid^%^20email^%^20profile&nonce=c20964d3bf5028ca156c06ef97319505]. The valid characters are defined in RFC 7230 and RFC 3986
org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:490)
org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:261)
org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:887)
org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1684)
org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
java.base/java.lang.Thread.run(Thread.java:834)
</pre><p><b>Note</b> The full stack trace of the root cause is available in the server logs.</p><hr class="line" /><h3>Apache Tomcat/9.0.43</h3></body></html>
I think part of the request is not good: “scope=openid^%^20email^%^20profile&nonce=c20964d3bf5028ca156c06ef97319505”
Curl is working propely with this parameter (without scope and nonce):
C:>curl "https://iamt.it:8443/openam/oauth2/realms/root/realms/OpenData/authorize?redirect_uri=https://ip/val/api/thirdparty_callback&client_id=xxxx.opendataclient&state=85ee872d7b81b5b5902a2f4926460ecf&response_type=code"
Is ok, return code is 0
Is like the problem we encountered in the previous case I post before: Error of the Callback of third party Oauth
-- scope request parameter is not required for authorization code grant
-- if (not isnull (scope))
-- params := params || sprintf ('&scope=%U', scope);
Let me know if everything is clear.
Regards.