Evaluation of the Log4J / CVE-2021-44228 vulnerability
Copyright (c) 2021 OpenLink Software support@openlinksw.com
Date: Mon Dec 13 2021
Introduction
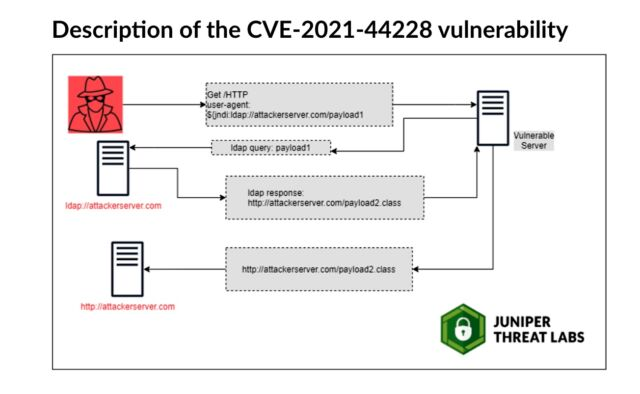
CVE-2021-44228, also known as the Log4Shell 0-day vulnerability, is the name given to a critical zero-day vulnerability that surfaced last Friday, December 10, 2021, when it was exploited in the wild in remote-code compromises.
Here is a brief description of the vulnerability courtesy of the Juniper Threat labs:
In this document we will document whether any OpenLink Software products are vulnerable and, if so, how the threat can be mitigated.
OpenLink Universal Data-Acces (UDA)
OpenLink Universal Data-Access Multi-tier components
All UDA Multi-tier components, such as the Request Broker, the Multi-tier Database agents, the Admin Assistant and the Multi-tier ODBC driver, are written in C, and therefore, they are not affected by this bug.
Our logging method does not allow for fetching and executing arbitrary payload from a remote service which is the root cause of this vulnerability.
OpenLink Universal Data-Access Single-tier components
All UDA single-tier drivers are written in C and therefore not vulnerable.
Our logging method does not allow for fetching and executing arbitrary payload from a remote service which is the root cause of this vulnerability.
OpenLink Universal Data-Acces JDBC Drivers
The UDA JDBC drivers do not use the Log4J API, and are not vulnerable to this style of attack.
NOTE: A third party Java application using the above driver could be installed with, or use a broken version of, the Log4J API. You should check with the vendor of that application to make sure it is not vulnerable.
OpenLink Universal Data-Access JDBC Bridges
The JDBC Bridges are not vulnerable to this type of attack, as they use our internal logging code which does not allow for fetching and executing arbitrary payload from a remote server/service.
NOTE: A third party JDBC driver, that itself uses a broken version of the Log4J API, could be vulnerable. You should check with the vendor of that driver to make sure it is not vulnerable.
OpenLink Virtuoso
The following paragraphs are relevant for all releases of both Commercial and Open Source versions of Virtuoso.
OpenLink Virtuoso Engine
The Virtuoso Engine is written in C and uses our own logging API which does not allow for fetching and executing arbitrary payload from a remote server/service.
Virtuoso ODBC drivers
The Virtuoso ODBC drivers are written in C and use our own logging API which does not allow for fetching and executing arbitrary payload from a remote server/service.
Virtuoso JDBC drivers
The Virtuoso JDBC drivers do not use the Log4J API, and are not vulnerable to this style of attack.
NOTE: A third party Java application using the above driver could be installed with, or use a broken version of, the Log4J API. You should check with the vendor of that application to make sure it is not vulnerable.
Virtuoso Jena, Sesame, and RDF4J providers
These providers do not use the Log4J API, and are not directly vulnerable to this style of attack.
NOTE: A Java application using any of the above frameworks could be installed with, or use a broken version of, the Log4J API, and therefore could be vulnerable. You should check with the vendor of that application to make sure it is not vulnerable.
Cloud images
Virtuoso Docker images
We scanned the packages installed on our Docker images and none of them install a version of the broken log4j.jar or log4j2.jar file or any of the packages flagged by RedHat or Ubuntu as being vulnerable.
Virtuoso PAGO and BYOL images on EC2 and Azure
We scanned the packages installed on our EC2 and Azure images and non of them have a version of the log4j.jar or log4j2.jar file installed, or any of the packages flagged by RedHat or Ubuntu as being vulnerable.
OpenLink DBpedia images on EC2 and Azure
We scanned the packages installed on our EC2 and Azure images and none of them have a version of the log4j.jar or log4j2.jar file installed, or any of the packages flagged by RedHat or Ubuntu as being vulnerable.
OpenLink Data Junction Box
We scanned the packages installed on our EC2 and Azure images and none of them have a version of the log4j.jar or log4j2.jar file installed, or any of the packages flagged by RedHat or Ubuntu as being vulnerable.
See Also:
- The official report on
CVE-2021-4422 - Article by Apache about the Log4J vulnerability
- Article by Ars Technica about the Log4J vulnerability
- Article by ZDNet about the Log4J vulnerability
- List of potentially vulnerable software, maintained by Dutch National Cyber Security Centrum
- List of affected RedHat packages
- List of affected Ubuntu packages