@cblakeley, but your fix is not online yet, right? (i tried a couple of minutes ago and the issue persists as of writing)
@turnguard: Not yet. Sorry for any confusion. We’ll post an update once the new VAD is available for download. /cc @hwilliams
@turnguard: A new 2.2.2_git197 VAL VAD is now available for download from http://download3.openlinksw.com/uda/vad-packages/8.2/val_dav.vad … please verify this resolves the issue you reported … /cc @cblakeley
@hwilliams @kidehen @cblakeley
RESOLVED:
i verified with my settings (see my twitter ACL above) and VAL VAD 2.2.2_git197 …
it works as expected: i get access denied with my google account and “yo, welcome” with my twitter account…
thanks a lot!
note: if you want to verify on my installation, just drop me your desired account and i’ll add an ACL for you.
account should be either google or twitter as of writing…
you have a google account? i would need to create a linkedIn dev account and setup a oauth client keys and stuff there? twitter is fine…
i added an ACL for your twitter account:
notes:
- google and twitter are already defined as IDPs
- you will be able to access my endpoint using your twitter account
- you WON’T be able to access my endpoint using your google account
- IMPORTANT NOTE: i created (you can sparql it then) your twitter ACL using HTTP (not HTTPS),
VAL.DBA.thirdparty_callbackcreates the service id using http
serviceId := sprintf ('http://twitter.com/%U', newUsr);
Yep!
It works!
Next, you should be able to emulate the OpenID Connect bindings along the following axis:
-
Solid Pods e.g., https://solid.openlinksw.com:8444 (NSS 4.x), https://solid.openlinksw.com:8445 (NSS 5.x beta), your own
-
OpenID Connect Idp instances of Virtuoso e.g., make another instance on another port that’s setup to be an OpenID Connect Idp.
Links:
the last link in your previous post [1] contains an image with your configured IDPs including solid pods [2]
can you share the configuration how you use an arbitrary solid pod as an IDP?
[1] x.com
[2] https://solid.mit.edu/
The process is very simple.
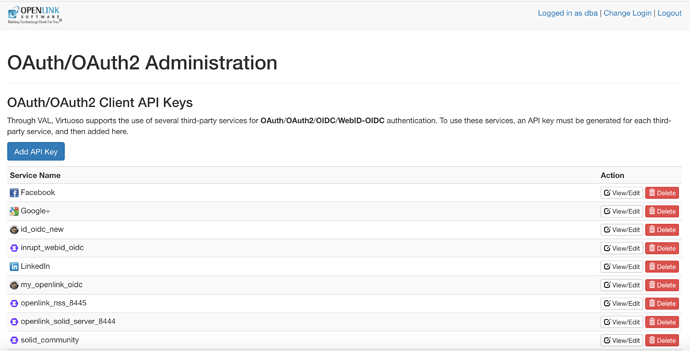
- Go to
<{your-virtuoso-instance-uri}>/oauth/admin - Click on Add API Key button
- Hatch the Dynamic Provider Information Discovery check-box
- Hatch the Dynamic Client Registration check-box
- Enter
{solid-pod-uri}for your Solid Pod - Enter
{solid-pod-uri}/registerfor your Solid Pod - Done
Screenshot 1
Screenshot 2
Screenshot 3
-
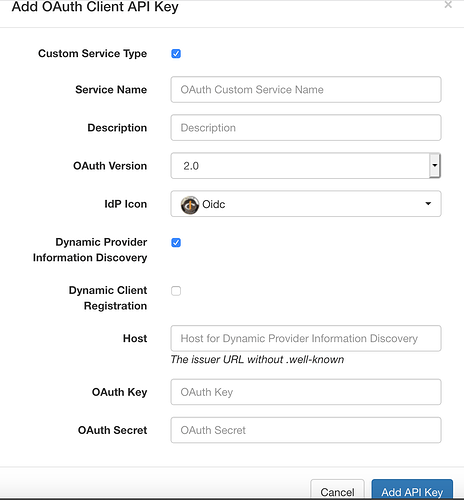
i hit “Add OAuth API key”
-
checked both checkboxes
-
enter my solid pod URI (https://solid.turnguard.com:8444)
-
here comes my micro issue:
i tried to enter https://gd.turnguard.com:8891/val/api/thirdparty_callback as the callback URL
when i hit the “Save” button, i got an error message (in red above the form): “Bad callback URI”
after a short investigation in/DAV/VAD/conductor/login_keys.vspxi found that there is a checktmp := VAL.DBA.http_to_https_uri ('http://' || VAL.DBA.val_cname ()); if (c_callback not like tmp) ... throw... 'Bad callback'tmp returns “localhost” no matter if i call conductor via my domain or on localhost…
anyway, i commented the check, then i could enter above callback uriEDIT: i have “localhost” in virtuoso.ini as DefaultHost… i haven’t tested, but after a check of
VAL.DBA.val_cname()that wouldn’t have occurred if i had gd.turnguard.com:8891 in my virtuoso.ini -
i added the following ACL…
PREFIX acl: <http://www.w3.org/ns/auth/acl#> PREFIX oplacl: <http://www.openlinksw.com/ontology/acl#> WITH <http://localhost:8890/acl/graph/rules/http%3A%2F%2Fwww.openlinksw.com%2Fontology%2Facl%23DefaultRealm> INSERT { <urn:rules:jj:oauth:oauth> a acl:Authorization ; foaf:maker <http://localhost:8890/dataspace/person/dba#this> ; oplacl:hasAccessMode oplacl:Read ; acl:accessTo <urn:virtuoso:access:sparql> ; acl:agent <https://solid.turnguard.com:8444/profile/card#me> ; oplacl:hasScope oplacl:Query ; oplacl:hasRealm oplacl:DefaultRealm . }
voila… !!
i can use my solid pod as IDP… very cool!
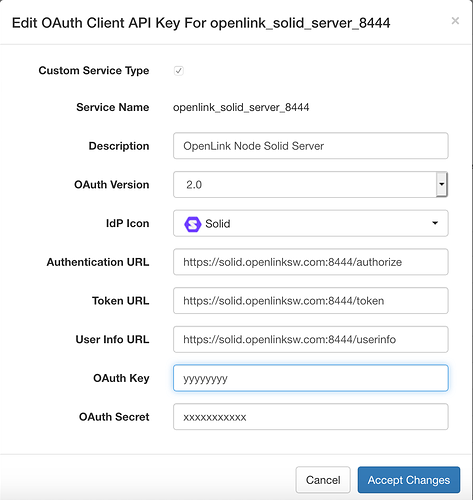
Wonderful! Note, you can pick the Solid Icon for your Solid IdP.
BTW – do you have screenshots for your Auth0 bindings?
Can I use this for some public demos, bearing in mind you’ve secured it? ![]()
re. auth0 i’m tempted to contribute a little piece of code…
it doesn’t work out of the box because auth0 can return user profile json constructs from various IDPs. All of them look different. note that VAL.DBA.thirdparty_callback procedure includes a switch to determine the serviceId depending on the IDP. so it would be necessary to create an own switch which is capable of handling different user profiles (e.g. from twitter, google, github, linkedin,…) and determine the serviceId from those. there is however a auth0 user api, that could return a unified profile for all of those IDPs… i need to investigate first…
note: i made it work in a couple of minutes by patching above callback procedure for the IDPs i want to use…
those user profiles are identifiable by a “sub” key in the returned json, the value of that key is the IDP + | + userId, so it’s not too hard to implement, e.g.
{
"sub":"google-oauth2|123456",
"family_name":....
....
re public demos: that would be totally fine with me… note however that i’m running a virtuoso 8.2. with a evaluation license on my notebook. so that’s not gonna be available much longer… ![]()
we’ve come very far with this thread… can we still elaborate how i can use virtuoso itself as an IDP?
i’ve created an application under /oauth using this callback
https://gd.turnguard.com:8891/val/api/thirdparty_callback
then i’ve then created a OAuth Service Binding, using
https://gd.turnguard.com:8891/OAuth2/authorize
https://gd.turnguard.com:8891/OAuth2/token
https://gd.turnguard.com:8891/OAuth2/userinfo
- the appkey and appsecret from the application i created under /oauth
when i use the respective login button on my /sparql endpoint, i’m taken to the login page, where i enter my dba credentials. after that i’m taken to the authorization page, where i click authorize… then i’m taken to the sparql endpoint, but am getting a message above the endpoint saying:
`Failed to fetch service ID from service “virtuosoods”.
(virtuosoods being the name of my OAuth Service Binding)
any hint?
`
To clear regarding the steps you followed:
OpenID Connect / OAuth Idp
-
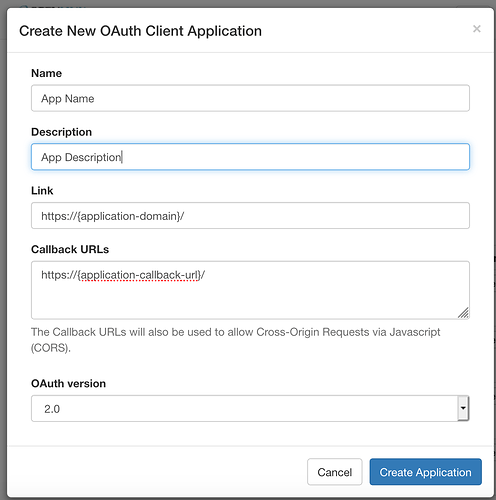
Go to
<{your-virtuoso-instance-uri}>/oauth/applications.vsp -
Click on Create Application button to get to the Application Creation/Registration Form
-
Fill in App Name field
-
Fill in App Description field
-
Fill in Link field with App Origin/Domain using pattern
<{your-virtuoso-instance-uri}> -
Fill in Callback URLs field with a Callback URL for app using pattern
<{your-virtuoso-instance-domain}/{callback-doc-name}> -
Click on Create Application Button
OpenID Connect / OAuth Relying Party (App or Client)
- Go to
<{your-virtuoso-idp-instance-uri}>/oauth/admin - Click on Add API Key button
- Hatch the Dynamic Provider Information Discovery check-box
- Hatch the Dynamic Client Registration check-box
- Enter
<{your-virtuoso-idp-instance-uri}>for Virtuoso-based OpenID Connect / OAuth IdP - Enter
{your-virtuoso-idp-instance-uri}/registerfor your Solid Pod - Done
Anything outside of the following re getting this to work amounts to some bug or quirk that we should resolve via this thread ![]()
/cc @cblakeley
i could make this work as well… for others to replay, i did the following with my domain https://gd.turnguard.com:8891
- go to
https://gd.turnguard.com:8891/oauth/applications.vsp
1.1. “Create New Application”
1.2. “Link” =>https://gd.turnguard.com:8891
1.3. “Callback URLs” =>https://gd.turnguard.com:8891/val/api/thirdparty_callback
1.4. “Create Application” (note: hit “View/Edit” to copy Application Key & Application Secret) - go to
https://gd.turnguard.com:8891/oauth/admin.vsp
2.1. “Add API Key”
2.2. “Service Name” => This Virtuoso
2.3. “Authentication URL” =>https://gd.turnguard.com:8891/OAuth2/authorize
2.4. “Token URL” =>https://gd.turnguard.com:8891/OAuth2/token
2.5. “User Info URL” =>https://gd.turnguard.com:8891/OAuth2/userinfo
2.6. “OAuth Token Key” => ${Application Key} (see 1.4)
2.7. “OAuth Secret” => ${Application Secret} (see 1.4) - Verification
3.1. go tohttps://gd.turnguard.com:8891/sparql
3.2. choose the “Virtuoso” icon under “More” button (alt: “Authenticate via This Virtuoso”)
3.3. redirected to:https://gd.turnguard.com:8891/oauth/authorize2(note: Link on login screen changed to “Authenticate to access: This Virtuoso Instance”
3.4. choose the “Twitter” icon under “More” button (note: i have the ACL for my twitter account already in place, @kidehen, you should be able to do the same with your twitter account, your google (or linkedin, github,…) account will get an access denied in the end)
3.5. hit the “Authorize app” button onapi.twitter.com/oauth
3.6. i’m redirected back to virtuoso’s authorization dialog athttps://gd.turnguard.com:8891/oauth/authorize2.vsp, hit the “Authorize” button
3.7. voila: i’m logged in and can access the endpoint
(note: there is a message: Failed to fetch service ID from service "thisvirtuoso"., this however can be ignored, the endpoint also presents a link to my twitter account next to “Logged in as…”
lovely! ![]()